Insider threat teams comprise some of the most critical elements of an organization’s security apparatus—yet they are often one of the least-funded groups. Increasingly, insider threat program managers are expected to do more with less, they often struggle to communicate the value their work generates, and they are left without unified support to fend off major risks.
The reasons for this phenomenon usually boil down to two fundamental factors: a lack of organizational trust and transparency. Inversely, when trust and transparency are both present, insider threat teams are empowered to do their best possible work.
The presence of trust and transparency in your organization means that your whole workforce believes you have their best interests in mind. The term “insider threat” can trigger negative associations with surveillance and monitoring. It’s critical that you counter these associations by communicating exactly what your mission is and precisely how you are carrying it out.
Trust and transparency will also help you gain a footing with executive leaders. Insider threat programs will always be a cost center, rather than a revenue generator. Senior decision makers, who are focused on bottom-line performance, need to see how your work connects to the overall success of the organization.
Being clear about your objectives, your track record, and the value of your work will help you justify the cost of insider threat programs when everyone is fighting for the same budget allocation.
"Trust and transparency mean that your whole organization understands the value of your work."
Foundations Of An Effective Insider Threat Program
If you’re committed to cultivating trust and transparency in your relationship with executive leaders, you’ll need to apply change management principles. Whether you’re standing up a brand new insider threat team, or trying to gain more support for an existing program, these four strategies will help you define and communicate your value.
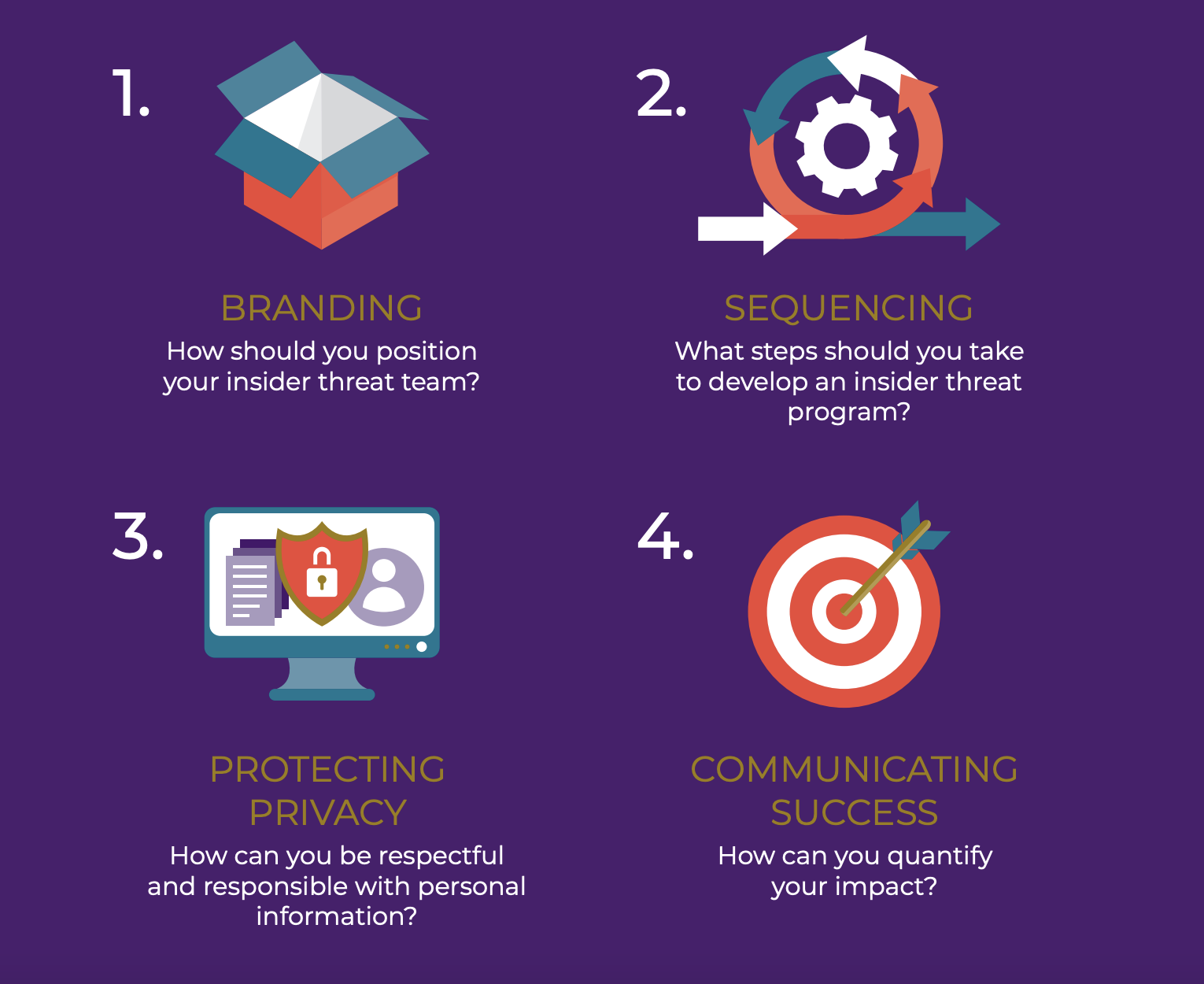
Strategy #1: Branding
Every security leader has a different opinion on what vocabulary to use: “insider threat,” “insider risk,” “insider trust”… But don’t let language get in the way of a more fundamental imperative: determining where your program is positioned within your organization.
What is your primary objective?
If your program is intended to mitigate theft, fraud, or workplace violence, Global Security might be a natural fit for the scope of your work. On the other hand, if you’re focused on protecting confidential and proprietary business information, it might make more sense to house your team within Information Security.
After you’ve determined where your program sits in the org chart, you should identify executive sponsors for your work. Ideally, this includes your direct supervisors, but sponsors can be anyone with a vested interest in the people, assets, or information you’re protecting. The important thing is having a clear line of communication to decision makers.
Finally, once your objectives, department, and sponsors are identified, you can turn your attention to the selection of a program name. Instead of settling on the most common industry terminology, challenge yourself to identify the name that best reflects your underlying strategy and your company culture.
For example, even if “insider threat” is the most universally accepted industry phrase, but your organization has a security culture oriented around risk, it may be more effective to use the term “insider risk.”
Branding is ultimately about alignment. You want your executive leaders and general workforce to understand exactly what you’re doing and why. By picking the right department, finding the right sponsors, and choosing a name that reflects your mission, you’ll set yourself up for an easier road ahead.
"Your program’s brand should help leaders understand exactly what
you’re doing and why."
Strategy #2: Sequencing
After you’ve put in the hard work of positioning and naming your insider threat team, you’ll quickly arrive at another hurdle: how to sequence the development of your program.
Effective sequencing strategy begins much the same way as effective branding. You first need to identify your objectives. However, at this point, you’ll need to get a lot more specific about the definition of success.
How will your performance be measured? What company assets are you trying to protect? Why did previous security measures work or not work?
Once your objectives are clear, it’s time to get to work.
Early on, insider threat teams will gain the most momentum by looking for easy wins with minimal friction. For example, you might begin by investigating employees who have recently left the company. The majority of internal theft happens within the last 90 days of someone’s employment, so you’re quite likely to find something worth pursuing. Since you’re investigating former employees, you’re also less likely to experience resistance from current team members.
You can also find early success by investing in basic email monitoring. Who’s sending messages from their work account to their personal account? Who’s sending messages to competitor domains or to the media?
Your goal shouldn’t be to intimidate employees looking for a new job or talking to news outlets. Instead, you can use this information to set healthy expectations: “Be smart about how you’re using company resources and software.”
Most importantly, as you make early progress, proactively share what you’ve found. You’ll demonstrate how quickly your team was able to generate value, which will make it easier to get additional support as you conduct trickier investigations. When you socialize exactly what you’re doing, you’ll also start to generate more leads from team members who trust you.
"Get early wins to gain long-term support."
Strategy #3: Protecting Privacy
Being able to catalog, retrieve, and protect information is a fundamental responsibility of insider threat teams. One of the best ways to bake privacy into your strategy is by investing in a quality case management tool.
Case management software like from Yakabod, makes it easy to document information in any form, helps you find new connections between data points, and enables secure sharing and collaboration.
But beyond your technology stack, protecting privacy depends on setting up checks and balances. Design these checks and balances to reinforce minimally invasive tactics. For example: Do you really need to see the content of emails, or can you draw valuable conclusions by just looking at the metadata?
You should set investigation procedures so that anyone conducting the investigation is unable to look at any content without having to go through another step or get approval from someone else. Get in the habit of documenting everything your team does or says, and keep it objective and procedural. (“How did you find that email?” “What was the source of that tip?”)
Protecting privacy will significantly impact the success of your team. In legal proceedings, it will give your organization credible and admissible evidence. When socializing findings, it will encourage your colleagues to trust your process. And it will signal to executives that you’re taking your role seriously.
Privacy also keeps you from undermining all the progress you’ve made. The minute you violate someone’s trust, your program will take a massive step back.
"Use minimally invasive tactics to earn trust."
Strategy #4: Communicating Success
Your organization’s industry will massively impact the way your leaders view security. For example, high-tech companies with large volumes of intellectual property are likely to value insider threat programs more than a manufacturing business with little IP to lose. Additionally, executives are usually most supportive when they’ve already dealt with a major, public threat.
But here’s the thing: every organization has dealt with an insider threat. The only difference is whether they know about it or not.
As an insider threat leader, your role is to point out the threats that already exist. One of the best ways to do that is by talking about your successful investigations with executives.
The key is to communicate clearly and often. Unfortunately, good news in the insider threat profession is rarely good news. If you catch someone leaking critical information, that means they were leaking critical information before you caught them.
By making security updates a habit, and sharing the highlights of every investigation with relevant leaders, you can put your findings in context. Suddenly, instead of wondering why you didn’t catch someone until it was too late, they’re seeing that you are actively mitigating threats on a weekly basis.
Communicating success will also have a positive impact on your overall success. As you share findings with the broader workforce, you reinforce expectations about your program and build a reputation for accuracy. That means potential bad actors are less likely to act maliciously, and colleagues are more likely to provide high-quality tips in the future.
"Mitigate threats with regular status updates to team members."
Getting Executives In Tune With Insider Threats
It’s time that insider threat programs claimed their rightful place at the center of organizational security strategy.
When you deploy thoughtful change management strategies to brand, develop, optimize, and share your team’s mission, you can help executive leaders see the value in your work—rather than focusing on the costs.
You can also transform skeptical coworkers into committed partners. Instead of asking, “Why do you need to watch our every move?” they’ll say, “I’m glad you’re protecting our team’s most valuable work.”
“At the end of the day, be clear about what you’re doing and what your mission is.”
-Charles Finfrock
This paper is based on an interview from the Yakabod Insider Threat Webinar Series with special guest Charles Finfrock.

|
About Charles Finfrock Charles Finfrock was Tesla’s first Insider Threat Program Manager, where he launched and implemented their program in North America, Europe, and China. Prior to Tesla, Charles spent 18 years with the Central Intelligence Agency (CIA) where he created and exploited insider threats in the hardest target countries and companies. Today he is the founder of the Finfrock Group, providing private intelligence and counterintelligence services to its clients. He can be contacted at https://vcci.io/. |