Every day, organizations face internal risks that endanger their most valuable information, assets, people, and operations. Insider threat program managers are the first line of defense Unfortunately, many program managers aren’t set up for success. Instead, they’re handicapped by a reactive stance that prevents them from effectively identifying and eliminating threats.
What causes this? Organizations often initiate their insider threat program for one of three reasons:
- They suffered from a successful internal attack.
- Their insider threat program is mandated by government requirements.
- They are following compliance standards and best practices.
The strategies that are driven by these motivations tend to be too narrowly focused and limit the likelihood of an insider threat program’s success. For example, if your program was created in response to a successful attack, it could be overly focused on preventing similar attacks. Similarly, if your program is mandated by the government or by general best practices, it might meet standard requirements, but not effectively address actual threats.
In other words, by taking a reactive stance, insider threat programs will never be set up to identify and respond to all of the signals that actually protect organizations from internal attacks.
Of course, your insider threat program likely falls somewhere in the middle. Maybe your work began in response to a successful attack or government mandate, but then evolved over time to incorporate new strategies, technologies, and techniques. But even if your insider threat program has been around for a while, how do you know if your strategy is working?
Let’s start with the warning signs. Here are common roadblocks to an effective insider threat strategy:
- Poorly defined or non-existent objectives
- Too compliance-focused
- Overly process-focused
- Not accounting for the human element
If your program checks the boxes for one or more of these obstacles, you’re not alone. They’re quite common. Most importantly, you have the opportunity to overcome them and start building a stronger insider threat strategy today.
"Most insider threat programs are too narrowly focused, which makes them less effective."
Foundations Of An Effective Insider Threat Program
The world’s most successful insider threat programs share a set of common traits. Their foremost characteristic is that they all take a proactive stance. This enables program managers to identify and mitigate threats before they turn into attacks. No doubt you’ve heard the “proactive versus reactive” mantra before. But how do you actually achieve a proactive posture? Here are four foundational strategies to pursue:
- Create a clear definition of success
- Secure buy-in from leadership
- Communicate a people-focused mission
- Invest in a culture of security, not just security tools
Of course, these strategies are easier said than done. You will need to tackle some major questions on your journey to best-in-class security: Should you focus on cybersecurity or human threats? How much do you invest in training versus technology? How can you move quickly while keeping your data secure?
The answer is usually balance.
There is never an easy, one-size-fits-all solution to insider threats, but the best program managers find ways to thread the needle between competing priorities. In the following pages we’ll explore three of the most critical “balancing acts” you’ll face when building the foundation for your own insider threat program.
"Taking a proactive stance will help you eliminate threats before they become attacks."
Balancing Act #1: Cyber Risk vs. Human Risk
Whatever form they ultimately take, insider threats are inherently human concerns. They are caused and shaped by human behavior. Even when insider threats take the form of a cybersecurity attack, people are at the core of the problem.
That means your cybersecurity tools and strategies will only ever be part of the solution. The best insider threat programs balance cyber and non-cyber indicators to get a clear picture of organizational risk.
What happens when your insider threat strategy is too focused on cybersecurity? First, by excluding human behavior from view, you will only see half of the true threat. Second, you will almost always act too late. (By the time an internal threat becomes a cybersecurity concern, it is too late to deter that attack from happening.) Third, you will have to manage vast amounts of data with little ability to prioritize, leaving your insider threat team to sift through an ocean of technical indicators and false positives. Finally, a cybersecurity-focused strategy makes it very easy for malicious actors to operate outside of the bounds of technology. If someone wants to harm your organization, they will find a way to do it creatively.
On the other hand, if you successfully balance both technical and non-technical indicators, you can build better visibility of the threats throughout your organization. You will empower your team to analyze cybersecurity data in context with the associated human behaviors for more effective detection. You will develop an understanding of the “why” behind certain malicious actions, while more easily finding patterns of behavior. And you will be able to shift your strategy from detection to deterrence.
"The best insider threat programs balance technical + non-technical indicators for continuous visibility."
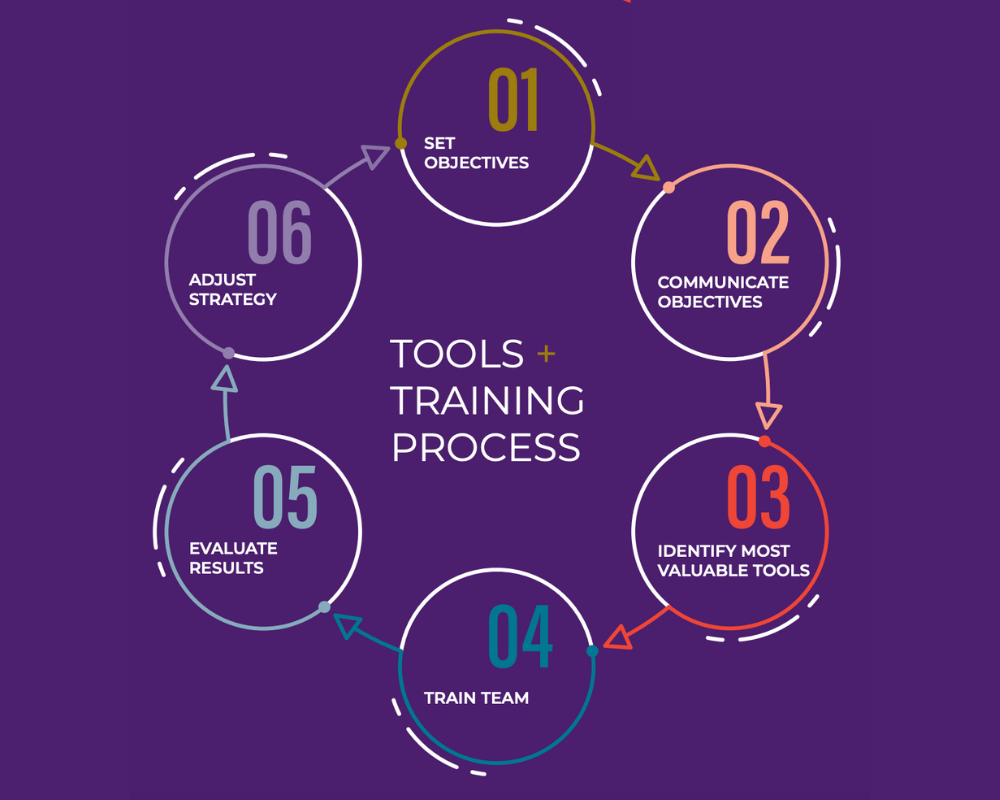
Balancing Act #2: Tools vs. Training
Security leaders often worry about what software and hardware tools they should buy to protect their organization, but easily forget their limitations. By nature, tools are only effective when they are aligned with a specific objective and operated by properly trained teams.
Before selecting a tool for your own insider threat team, first consider the goals you want to achieve. Will this new technology get you closer to achieving your definition of success? When evaluating budgets and making procurement requests, get in the habit of connecting those requests back to your organization’s larger objectives. In other words: Build tools around your program, not the other way around.
"Build tools around your program, not the other way around."
After you’ve found the right technology suite for your program comes the most critical part: training your team. Training is more nuanced than many security leaders think. When done well, it involves educating the general workforce and investing in the technical proficiency of your insider threat team.
Your colleagues are ultimately your best line of defense against insider threats. You need a capable and dedicated workforce if you hope to be effective. That’s where regular messaging and communication come into play. Let employees know: Why does your insider threat program exist? How are employees expected to act? What should they do if they notice something specific? Get in the habit of talking about the human element of your program— both threats and solutions—to build a shared vision and cultivate trust.
Alongside this broader communication strategy, you must be ready to invest in tactical training for your insider threat experts. This kind of training is never a one-off event; it should be happening continuously and regularly as your risk exposure and security stack evolve. By integrating training into your routine, you’ll be able to spot weaknesses in your strategy and increase your team’s technical competence when a real threat emerges.
If you and your team members have a clear mission, tools to achieve that mission, colleagues that are willing to work with you, and the right skillset, your organization will be safer than ever.
"Effective training includes educating your workforce + investing in technical proficiency."
Balancing Act #3: Confidentiality vs. Efficiency
One of the biggest challenges any insider threat program manager faces is knowing how to manage sensitive data and confidential information. Insider threat cases are never anonymous cases—they involve and impact real people. That’s why it’s critical to treat the people involved (and their information) with utmost care and respect. Moving quickly is important, but moving carefully and securely is even more essential.
If your program exists to protect people, betraying their confidentiality will undermine the very foundation of your insider threat program. Getting it wrong can ruin an innocent person’s career, and it will also erode the confidence of your leadership team and general workforce. When you lose that buy-in, you may even lose funding—which leaves your organization more vulnerable to insider threats than ever before.
To maximize the integrity of your investigations, it’s critical to build workflow processes and use case management tools that optimize both efficiency and confidentiality.
Limiting access to insider threat data is a great place to start. When every file, document, and message is shared on a need-to-know basis, you can evaluate threats in a manner that protects people, protects your organization, and improves results.
Separating data is another critical strategy. By storing case data in its own dedicated repository, you're further limiting the chances of an unauthorized individual accessing it or a bad actor exploiting it. Finally, your case management system should be self-contained and streamlined. Ad hoc tools like spreadsheets and email make it nearly impossible to protect sensitive data; instead, look for tools with in-app private messaging and purpose-built workflows.
"The right case management system will help you evaluate threats by working efficiently and protecting people at the same time."
Conclusion
New insider threat tools are coming out every year. But studies show that the prevalence of insider threats is only increasing. Why is this happening?
Clearly we need more than high-tech software to protect our organizations. If we really want to stop insider threats, we need to embrace the messy, human side of the security equation. How can you set your program up for success today? Start by creating a clear definition of success. Step back and ensure that your strategy is carefully aligned with your organizational objectives and socialized with all the relevant stakeholders. Otherwise, you might be doubling down on approaches that aren’t working.
Then, take some time to apply the three fundamental balancing acts to your own work:
- Focus on people and human behavior, not just technical indicators
- Invest in training, education, and socialization throughout your organization
- Buy tools that complement your strategy and keep your data safe
“We should approach confidentiality and privacy from the standpoint of protecting people first.”
- Virgil Capollari
This paper is based on an interview from the Yakabod Insider Threat Webinar Series with special guest Virgil Capollari.

|
ABOUT VIRGIL CAPOLLARI Virgil Capollari is a former U.S. intelligence officer and founder of Adaptive Risk Strategies. Virgil spent decades managing and countering internal threats in a government context. Today, he leverages his expertise to help security professionals, private companies, and organizations improve their own insider threat and corporate counterintelligence strategies. He can be contacted at www.adaptive-risk-strategies.com. |